GCSD works with FBI to investigate cyber attack
— Photo from CISA’s Top Tips for Virtual Learning
For at-home remote learning, the federal Cybersecurity and Infrastructure Security Agency recommends use of: parental controls, a virtual private network, multi-factor authentication, and a password manager. The agency recommends against opening unknown email attachments and opening links from unknown sources.
GUILDERLAND — The school district here is working with the FBI and with “a number of subject matter experts” to investigate a cyber attack that occurred on Thursday, April 22, according to Superintendent Marie Wiles.
In-person classes for seventh- through 12th-graders were canceled on Friday, Monday, Tuesday, and Wednesday due to the attack. Hybrid instruction was scheduled to resume on Thursday, April 29.
“Because our investigation and response are ongoing, I cannot, at this time, provide additional details about the incident, or specific actions taken to secure our network,” Wiles responded in an email on Tuesday to a series of questions from The Enterprise.
“However,” she went on, “our community can rest assured that we are taking all appropriate precautions to restore our systems in a safe and secure manner and we will be incorporating additional technologies into our cybersecurity program as we move forward.”
Since the onset of COVID-19 and the increase in remote learning in schools, “malicious activity with ransomware attacks against K-12 educational institutions” has risen sharply, according to the Cybersecurity and Infrastructure Security Agency (CISA), an independent federal agency under the oversight of the Department of Homeland Security.
The Guilderland schools reopened in September, offering any students who chose to, to learn remotely at home. Elementary students were offered in-person classes, seated six feet apart in classrooms, while Guilderland High School students follow a hybrid schedule, alternating in-person and remote classes.
“Malicious cyber actors are targeting school computer systems, slowing access, and rendering the systems inaccessible to basic functions, including remote learning,” says a fact sheet that CISA developed with the FBI for schools. “In some instances, ransomware actors stole and threatened to leak confidential student data unless institutions paid a ransom.”
While Wiles was unable to comment on whether the Guilderland schools had been told to pay a ransom when some of their systems were encrypted, she did email on Sunday, “At this time, we have not confirmed that any sensitive data was compromised, but we will update you as more information becomes available.”
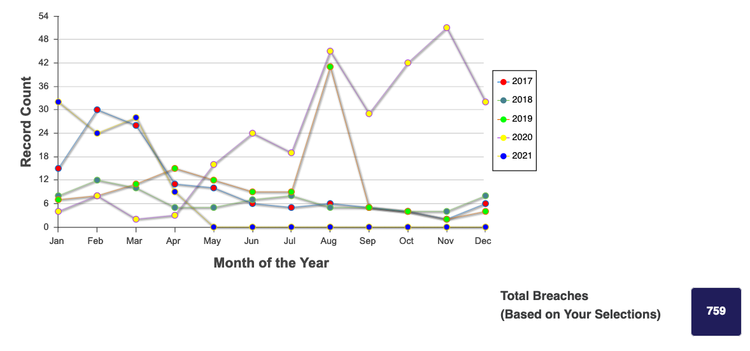
This graph from the not-for-profit Identity Theft Resource Center shows a huge spike in the United States of breeches in education systems since March 2020, totaling 759 since 2017.
Ransomware, explains CISA, is an ever-evolving form of malware designed to encrypt files, making them unusable. Malicious actors then require ransom payments to re-open the files.
“Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid,” says CISA.
Wiles wrote in her Sunday email that Guilderland’s cyber attack was by “a threat actor group which used malware to encrypt certain GCSD system throughout the district.”
Since March, the CISA fact sheet says, uninvited users have disrupted live-conferenced classroom settings by verbally harassing students, displaying pornography and violent images, and doxing meeting attendees. Doxing means to publicly identify or publish private information about someone.
A December report by the Joint Cybersecurity Advisory — coauthored by the Federal Bureau of Investigation, the Cybersecurity and Infrastructure Security Agency, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) — says that cyber actors likely view schools as targets of opportunity.
According to MS-ISAC data, the percentage of reported ransomware incidents against K-12 schools increased at the beginning of the 2020 school year. In August and September, 57 percent of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to 28 percent of all reported ransomware incidents from January through July.
“Whether as collateral for ransomware attacks or to sell on the dark web, cyber actors may seek to exploit the data-rich environment of student information in schools and education technology (edtech) services,” says the Joint Cybersecurity Advisory report. “The need for schools to rapidly transition to distance learning likely contributed to cybersecurity gaps, leaving schools vulnerable to attack.
“In addition, educational institutions that have outsourced their distance learning tools may have lost visibility into data security measures. Cyber actors could view the increased reliance on — and sharp usership growth in — these distance learning services and student data as lucrative targets.”
The FBI and CISA recommend schools review or establish patching plans, security policies, user agreements, and business continuity plans to ensure they address current threats posed by cyber actors. The report provides lists of “best practices” for networks, for user awareness, for video-conferencing, for ed-tech implementation, and for malware defense.
CISA provides a plethora of online materials — from tip sheets to webinars — to inform students, parents, teachers, and administrators. Advice includes that staff and other network users avoid public Wi-Fi, that administrators turn off anything that might allow remote access when not in use, that software patches be kept up to date, and that schools have back-up systems to recover data.
“Data breaches do not typically happen when a cybercriminal has hacked into an organization’s infrastructure,” notes one recommendation on a tipsheet. “Many data breaches can be traced back to a single security vulnerability, phishing attempt, or instance of accidental exposure. Be wary of unusual sources, do not click on unknown links, and delete suspicious messages immediately.”
Phishing schemes, another tipsheet explains, are used by cybercriminals to lure users to click on a link or open an attachment that infects their computers, creating vulnerability to attacks. Phishing emails may appear to come from a real financial institution, e-commerce site, government agency, or any other service, business, or individual.
Victims of ransomware are advised to report it immediately to CISA at www.us-cert.gov/report, a local FBI Field Office, or Secret Service Field Office.
GCSD update
Wiles emailed Guilderland school families on Tuesday evening that in-person classes for secondary students will be delayed at least another day.
“Throughout the day today, our technical team continued to remediate and test our internet system to ensure a successful return to stable, reliable internet connectivity for a seamless transition to onsite learning,” Wiles wrote. “As the day progressed, testing began to show some instability with the connection on some devices. Despite our continued work around the clock to return to hybrid learning, we need more time.”
She went on, “As a result of this decision, there will be no state assessments administered for grade 8 students, as originally planned. Fully remote teachers will also continue to teach from home K-12. “
More information will be shared with staff and families about the process to resume the safe use of school-issued devices, Wiles said, before people return to the school buildings.
She also wrote that new software on district hardware “adds a higher level of protection, to reduce the likelihood of an incident of this nature and magnitude in the future.”
Guilderland School Board members met in executive session on April 28 to discuss the matter and plan to update the public at their May 4 meeting.



